Is it possible to eliminate ransomware from your Mac?
If you find yourself among the unfortunate few grappling with the removal of Mac ransomware and the challenge of recovering encrypted files, rest assured that while both tasks are achievable, they may not always be straightforward. We must be honest: in certain scenarios, recovering files may be an insurmountable challenge. As cybercriminals craft more advanced ransomware attacks, victims, whether Mac or Windows users, find it increasingly difficult to retrieve their files.
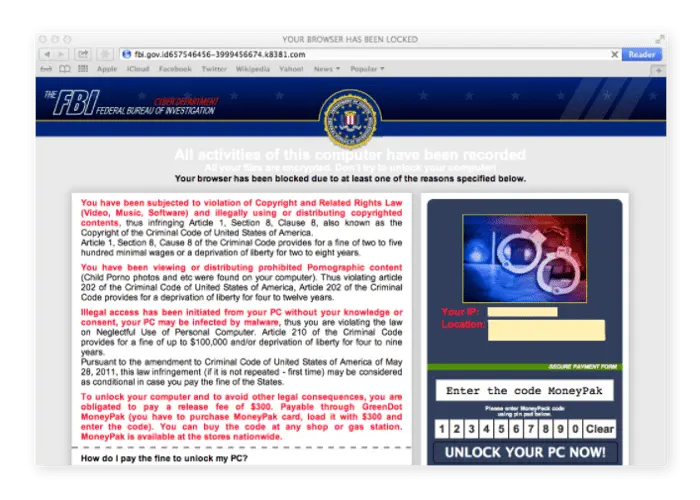
The type of attack dictates how easy or hard it is to remove Mac ransomware. For instance, the browser-locking FBI / MoneyPak scam can be eliminated in just a few minutes. Conversely, encryption ransomware presents a formidable challenge. Known also as filecoders, these types of ransomware encrypt your files, blocking access to them. In such cases, merely removing the ransomware is only a partial victory; decrypting your data is the critical step for file recovery. Cybercriminals exploit the difficulty of this task, demanding payment for a decryption key to unlock your files.
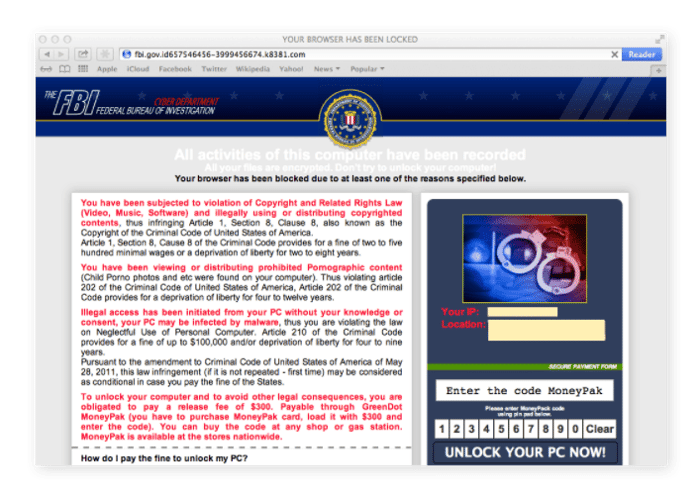
Image source: https://cdn2.hubspot.net
Each filecoder employs a unique encryption technique, making its removal and recovery more complex compared to other malware types. To protect your Mac from ransomware and eliminate it should a strain manage to infiltrate, Avast One is a reliable solution. While it may not always undo the encryption, it effectively prevents the ransomware from spreading across both private and public networks your Mac connects to.
STEP 1: Immediately isolate infected devices
If your Mac is infected with ransomware, immediately find and disconnect all infected wired and wireless computers, tablets, and smartphones on your network, regardless of their operating system. This keeps the malware from spreading to other computers and/or mobile devices.
As you take care of this, make sure you disconnect everything connected to the devices on your network, including:
- Shared and unshared network drives
- External hard drives
- Flash drives
- Cloud storage accounts
If you think any of these devices were connected to the infected computer, check their systems for ransomware as well.
STEP 2: Find out which strain of Mac ransomware is on your computer
Once the infected devices have been isolated, identifying the specific type of Mac ransomware is crucial. This understanding can pave the way to resolving the issue. Among the most challenging types of ransomware to contend with are filecoders, such as KeRanger or MacRansom. Conversely, other variants like screenlockers are typically less complex to eliminate. Below is a succinct overview of the most prevalent forms of Mac ransomware.:
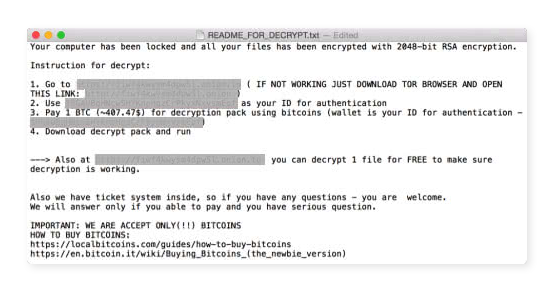
- Filecoders encrypt and lock files on your Mac. The cybercriminals behind this type of ransomware demand payment for decryption keys, usually by a deadline, at which point they promise to damage, destroy, or permanently lock your files. Around 90% of ransomware strains are filecoders.
- Image Source: https://167974-484938-raikfcquaxqncofqfm.stackpathdns.com
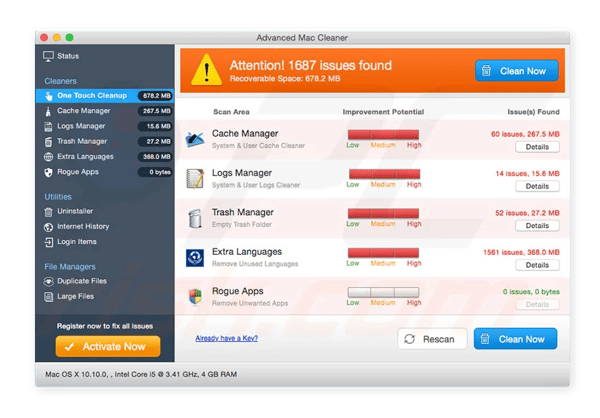
- Scareware opens pop-up ads, fake web pages, or a scanning application with fake results, all pushing you to pay for a bogus Mac malware cleaner to remove issues that your computer doesn’t have. As long as you don’t click on the ads, pages, or app, you can get rid of this type of ransomware easily.
- Image Source: https://www.pcrisk.com
- Doxing represents the potential release of sensitive personal information, including usernames, passwords, email addresses, and credit card details. Although not classified as malware, doxing operates on a ransom basis: victims receive a notification that cybercriminals possess their confidential data and will release it on the Dark Web unless a payment is made. To counter this threat, our Avast Hack Check tool offers a free service to determine if your passwords have been compromised or stolen, while our advanced tool for checking identity theft ensures comprehensive protection of your data.
- Screenlockers serve a simple yet disruptive purpose: they prevent access to your Mac by locking the screen. The most prevalent type encountered is the FBI/MoneyPak scam, which specifically targets your Safari web browser, locking it and then demanding a ransom for its release. While screenlockers are more frequently found on Android devices, it’s crucial to exercise caution when using Safari to avoid falling victim to these schemes.
As a Mac user, you can rest a bit easier than Windows users, but that doesn’t mean your machine is immune. All four threats listed above can infect unsuspecting Mac and iOS device users, too — it just takes one bad click or tap!
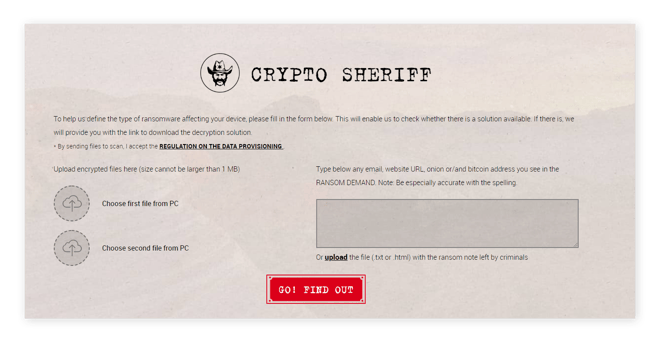
Use Crypto Sheriff’s tool to identify the strain of Mac ransomware
To identify the specific ransomware affecting your Mac, we advise utilizing the Crypto Sheriff tool offered by Europol’s European Cybercrime Center, part of the No More Ransom project. This efficient tool examines your encrypted files and the ransom note. If Crypto Sheriff identifies the ransomware and has a decryption solution available, it will supply a direct link to download the necessary decryption software for your Mac.
Visit tech forums to learn more about the types of Mac ransomware
For assistance with Mac ransomware strains, consider exploring troubleshooting and tech support forums. These platforms often host up-to-date discussions, potentially offering solutions for new variants or collaborative efforts to tackle the issue.
Many Mac ransomware infections, such as FindZip, generate files named “README.txt”, “DECRYPT.txt”, or “HOW_TO_DECRYPT.txt”, placing them either on your desktop or within system folders. Additionally, they may alter filenames and extensions, such as .docx or .dll. When seeking help on tech forums, using these filenames as search queries can direct you to relevant threads that provide insights into removing the specific ransomware affecting your Mac.
We recommend visiting these forums:
STEP 3: Eliminate ransomware malware from your Mac
Once you know what you’re dealing with, you can start the Mac ransomware removal process. You have four options:
- Wait for the ransomware to delete itself (which it often will)
- Get rid of it with Avast One
- Have our experts at Avast Premium Tech Support remove it
- Remove the malware manually
Option A: Check if the ransomware program deleted itself
In many cases, the ransomware on your Mac simply removes itself after encrypting your files. Cybercriminals want their malware to survive in the wild; therefore, they don’t want it leaving behind clues that could crack their strain’s encryption and render it harmless.
Option B: Remove the malware with free Avast Security
Avast One offers a complimentary solution for swiftly detecting and eliminating prevalent ransomware threats. This tool not only secures your Mac against emerging cyber threats but also efficiently identifies and removes Mac ransomware. Additionally, its free version provides an added layer of protection against new ransomware variants, preventing your files from being encrypted.
Option C: Let Avast Premium Tech Support remove Mac ransomware for you
Contact our specialists at Avast Premium Tech Support (APTS) for comprehensive assistance in removing ransomware from your Mac. APTS, a premium service, provides round-the-clock support for both hardware and software challenges. While our experts are adept at removing ransomware, please note that retrieving encrypted files falls beyond our scope of services.
Option D: Remove Mac ransomware manually (ADVANCED MAC USERS ONLY)
In most cases, one of the three options listed above will be all you need to remove ransomware from your Mac. However, ransomware attacks are constantly evolving and growing in number, so there is always the possibility of getting hit with a strain that none of the aforementioned methods can handle. In that case, you might feel your only option is to clean your Mac yourself.
Should you choose the DIY approach, we highly advise beginning with the aforementioned online forums. These platforms are dedicated to staying abreast of the latest ransomware trends and swiftly devising solutions, ensuring you receive reliable advice from their members.
STEP 4: Recover your encrypted files
You’ve removed the underlying malware, but that alone won’t recover your files. Here are a few methods that can help you get your files back:
Option A: Restore your system from a backup
You can get your Mac back up and running easily if you’ve been backing up its operating system. Ridding your computer of the malware that’s locking your system or holding your files hostage will stop encryption from spreading through your Mac and network, which means you can still recover your files from a backup.
The backup recovery method is highly effective when you’re dealing with a pesky screenlocker, which doesn’t encrypt your files. Even though you’re more likely to be wrestling with a filecoder that keeps you from accessing your files through — you guessed it — encryption, you can still use your Mac’s Time Machine to roll your system back to its “pre-attack” state and restore encrypted files. So, if you’ve set your Time Machine up to do automatic backups, your files are ready and waiting for you to recover them.
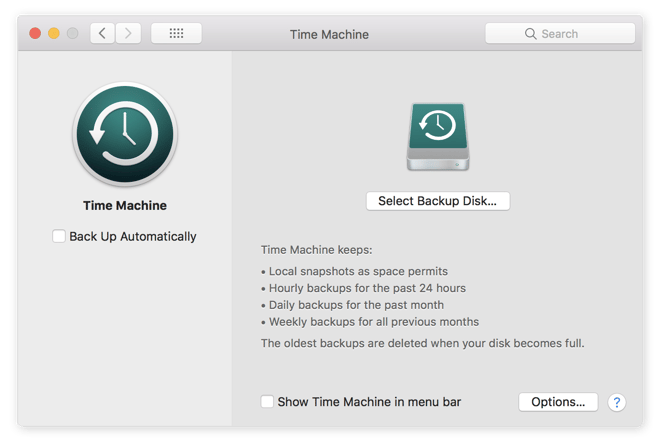
Image Source: https://support.apple.com
Also be sure to take a look inside your iCloud account, as you might have unencrypted backups of personally valuable files like photos and documents created with Apple applications.
As a last resort, you could also use file recovery software like Wondershare Data Recovery for Mac.
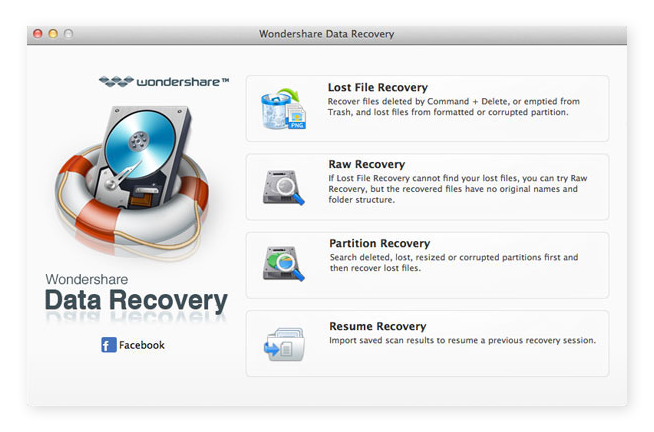
Image Source: http://www.recuvaformac.com
Option B: Use decryption tools
Should the ransomware identification techniques mentioned previously confirm that a filecoder has compromised your Mac, encrypting your files, you might find solace in a decryption program to retrieve your data. Fortunately, for victims of the FindZip strain, we offer a specialized tool designed to facilitate the decryption process efficiently.
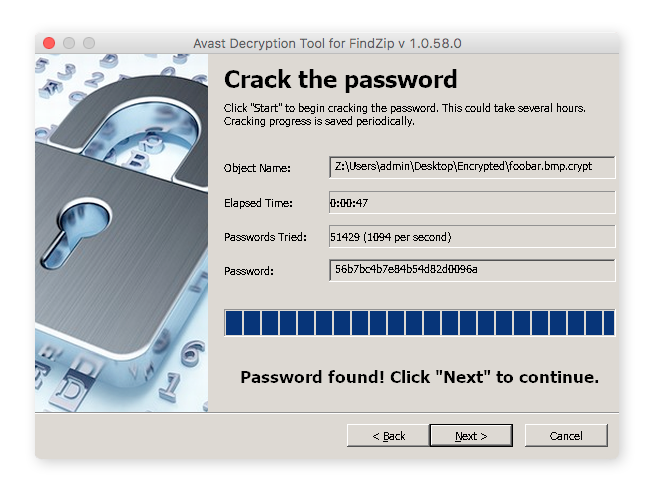
Although the majority of our Avast decryption tools are designed for Windows PCs rather than Macs, it’s worth exploring them. They provide detailed information on known ransomware strains, including filename alterations and ransom notes, along with a free downloadable decryptor for each variant.
Regrettably, most ransomware types remain undecrypted, leaving no available tools to recover your files. In such instances, your best bet is to restore files from a backup or wait for the development of a free decryption tool capable of tackling the ransomware strain affecting your Mac.
Option C: Avoid paying the ransom and refrain from negotiating.
If you still can’t recover your files after following all the instructions above, we strongly recommend waiting for a decryption tool for the strain of ransomware on your Mac. Sometimes, the malware exposes lines of code that can lead to a fix.
 If you get hit with ransomware, don’t pay the ransom.
If you get hit with ransomware, don’t pay the ransom.
We recognize your urgency in recovering your files, but strongly advise against paying the ransom. Equally, negotiating with the attacker of your Mac should be avoided. Succumbing to their demands not only fuels the cycle of ransomware by motivating perpetrators to continue hijacking devices and innovating new threats but also potentially finances other unlawful endeavors.
One crucial point to remember is that paying the ransom does not ensure that the hacker will remove the ransomware, unlock your device, or provide you with the necessary decryption tool. While many cybercriminals aim to build a reputation for reliability to encourage future victims to pay, this outcome is far from guaranteed. There have been numerous instances where offenders have taken the ransom only to disappear or provide ineffective decryption tools. Worse still, victims might find themselves inadvertently funding a completely different ransomware attacker.
Common Questions
These are some of the most frequently asked questions about Mac ransomware.
Can Macs get ransomware?
Let’s get one thing straight: Macs are not immune to ransomware or any other form of malware.
There was a period when Macs appeared virtually impenetrable, largely because cybercriminals targeted Windows computers, attracted by their larger and more profitable user base. Apple’s macOS, formerly known as OS X, boasts robust built-in defenses that make it harder to breach. Indeed, Macs are immune to certain ransomware like WannaCry, which exploits vulnerabilities unique to Windows systems.
However, the landscape is evolving. Mac attackers are relentlessly crafting new malware, rendering mere reliance on macOS’s inherent security insufficient. Although PCs are generally more susceptible to attacks, Macbooks and iMacs also require dedicated security measures. According to backup provider Datto’s 2018 Ransomware Report, ransomware attacks on Mac computers surged by 500% in a single year, highlighting the growing need for comprehensive Mac security protection.
How common is Mac ransomware?
The rise of Mac ransomware over the past couple of years is cause for concern — it exists and is likely to continue growing. While it is relatively rare compared to ransomware that targets Windows and mobile operating systems, you should still be vigilant when you’re online and take appropriate measures to keep your Mac safe. Just one ransomware infection could ruin your life. Seriously: imagine losing all your photos, videos, documents, and so on, business and personal. Now, take a few minutes to implement the preventative measures we’ve suggested so that scenario stays in your imagination.
Are Mac browsers vulnerable to ransomware?
Cybercriminals have also targeted Apple’s recommended browser, Safari. The most well-known Safari ransomware strain is the FBI / MoneyPak virus we mentioned above. Be careful where you click, and what you download!
Set up your defenses against Mac ransomware
Securing your Mac and ensuring your peace of mind starts with preemptively blocking ransomware infections. Begin by configuring Time Machine for automatic, scheduled backups. For added security, store critical files in iCloud and on a physical device like an external hard drive or USB stick. Consider it akin to regular dental check-ups: often neglected until pain arises, yet essential for preventing cavities—or in this case, ransomware. Commit to regular file backups (and perhaps, make this the year you start flossing regularly too).
Enhance your Mac’s protection at no cost with Avast One. This tool swiftly identifies and eliminates known ransomware variants while protecting against the latest threats and preventing file encryption.
In summary, safeguard your system and files, fortify your Mac with dependable anti-malware, and remain cautious online. Ransomware threats to Macs persist, but by adopting these strategies, you’re far more likely to read about them than to experience them firsthand.